SIEM
SureLog SIEM
The ultimate goal of the compliance (PCI, GDPR, HIPAA, SOX, GLBA, ISO 270001 etc.) is to ensure data security in all possible ways. This means you should instantly detect suspicious activity occurring in your network, analyze it quickly to validate whether it’s a potential threat, and if so, take remedial measures immediately to stop future breaches. SureLog’s out-of-the-box advanced correlation rules can automate these workflows for achieving and maintaining compliance. SureLog enables a “collect once, comply with many regulations” methodology for meeting compliance requirements and keeping cost to a minimum.
Under the GDPR mandate, an organization has 72 hours to alert all affected parties and appropriate regulatory bodies. Collecting massive security event data from everywhere in your IT ecosystem is a challenging task. This is where SureLog steps in. SureLog is capable of collecting and aggregating security events from all endpoints, servers and security tool tack. Thanks to pre-build GDPR mappings and GDPR compliance reporting, SureLog helps your organization to comply GDPR mandate.
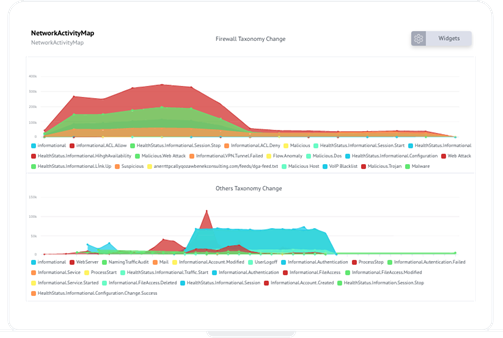
Advanced Correlation
SureLog correlation engine identifies and responds to complex and oftentimes undetectable operations events in real-time.
UEBA and Profiller
SureLog will track logins from countries on a per user basis, baselining log in countries for the past 30 days. Once a user authenticates from a location not seen in that period, the rule will trigger.
Expect More Pay Less!
Price matters. SIEM products are differentiated by cost, features, and ease of use. It is known that the more you pay, the greater the sophistication SIEM tool you have. But with SureLog, you do not pay more.
MEET SECURITY AND COMPLIANCE REQUIREMENTS WITH MOST AFFORDABLE SIEM – SURELOG
SureLog is a next-generation Security Information and Event Management (SIEM) tool that monitors logs from network hardware and software to spot security threats, detect and prevent breaches, and provide forensic analysis. Surelog SIEM will help your organization:
- Monitor anomalous access – Instantly identify potential unauthorized access to your critical assets from suspicious locations
- Identify compromised credentials – Seamlessly spot user impersonation and compromised user or system accounts
- Track user account creation – Report suspicious account creation and account management activities to security and HR teams
- Monitor crown jewel assets – Identify all monitoring and traffic to your most critical assets in real-time
- Monitor privileged users – Track all privileged user connections to crown jewel or executive assets by non-privileged or non-executive users
- Monitor failed login and locked accounts – Get instant notification on suspicious login attempts and locked accounts due to high number of logon failures
- Monitor remote access – Identify risky VPN access
- Prioritize security alerts – Assign risk ratings to various security alerts and notify security incident teams automatically as per the high priority items
- Monitor data exfiltration – Spot risky session trying to exfiltrate data
- Monitor email, database, and web traffic and endpoints – Identify risky email, database, endpoint and web data exfiltration attacks
NEED MORE INFORMATION?
Didn’t find what you were looking for or need more information or want a quote. Fill out the form on the side and our expert consultants will reach you as soon as possible…















