CITRIX WORKSPACE
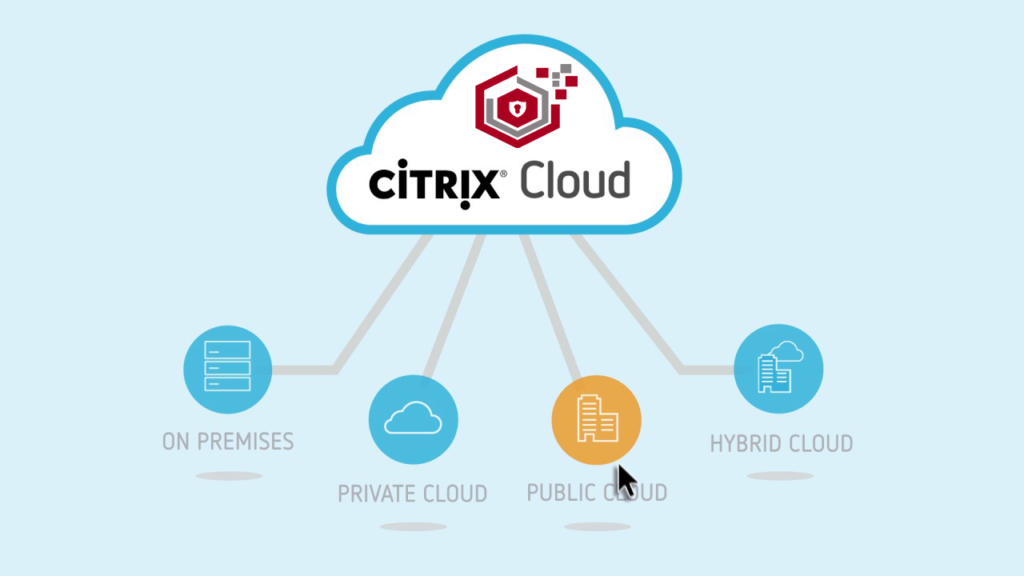
This article describes the capabilities and architectural features of the Citrix Cloud platform and Citrix Workspace service pack from SecroMix partners. These solutions are the central element and foundation for the implementation of the digital workspace concept from Citrix. Let’s try to understand and formulate causal relationships between cloud platforms, services and Citrix subscriptions. The […]